Journalists for Human Rights NGO’s http://forrights.am website has been regularly subjected to DDoS attacks since December 12, which have left the site’s operation in full disruption for several days.
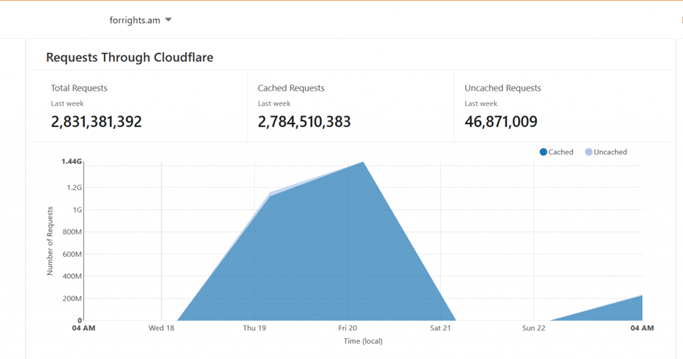
DDoS attacks on Forrights.am site
The CiviCERT-AM team took over protection of the site since December 18, moving it to a new server and bringing the site under Cloudflare protection. In just 4 days, the adversary party has concentrated considerable resources towards Forrights.am, with over 2.8 billion queries over 10 terabytes, and attack speeds regularly reaching 150k / RPS (150,000 queries per second).
“I have strong doubts as to who authored it. We are covering a criminal case involving one of the most famous oligarchs,” commenting on the attack, wrote Forrights.am editor Zhanna Alexanyan on Facebook. – “This oligarch has great influence in Armenia to date, as you can see also in issues restricting freedom of speech.”
This attack, lasting and unprecedented by its dimensions, is violation of freedom of speech, and the CiviCERT-AM team announces that they will do their best to make sure Forrights.am continues its operation and exercises its right to receive and disseminate information.
History of DDoS attacks in Armenia
Let’s point out that DDoS attacks are not new to Armenia. They have been regularly used in the Armenian-Azerbaijani cyber conflict since the early 2000s. Thus, in 2005, almost all Armenian forums were under strong DDoS attack for about two weeks.
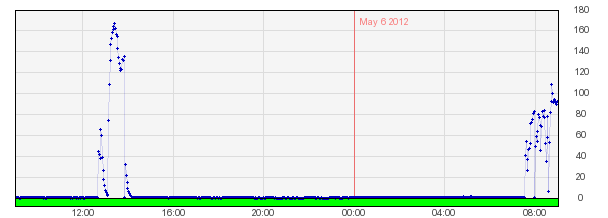
DDoS
An attack on iDitord.org website
In domestic contexts, such attacks began to take place in 2012. Thus, during the parliamentary election campaign phase, in late April – early May, several websites were subjected to attacks. The first was the pre-election campaign site, posor.am, which was flooded with black PR material, which was closed at that time and is only available in the archives. Then 1in.am, blognews.am fell under attacks and, on election day, May 6, the iDitord.org platform was out of order for several hours for reporting electoral violations (the latter was created by members of today’s CiviCERT-AM team).
Subsequently, such attacks periodically occurred. Thus, for example, in 2013-2014 a number of attacks were carried out, of which neither the target nor the author became known, but their intensity was such that they resulted in communication failure at the state level.

